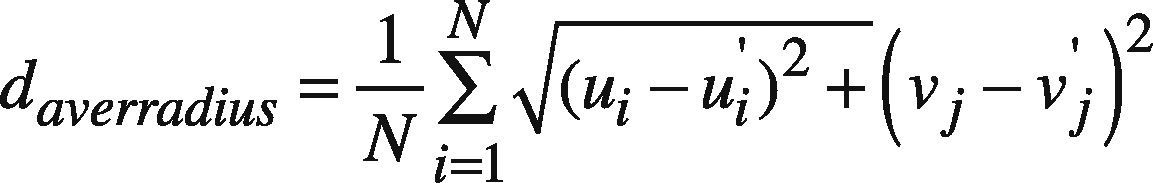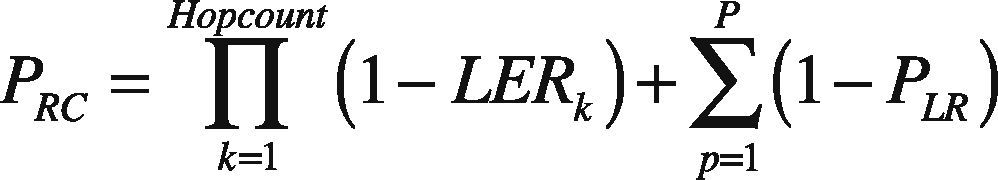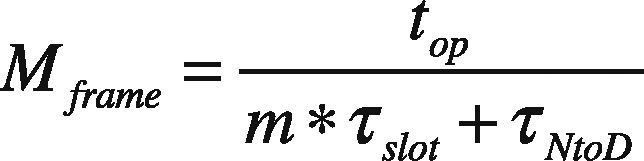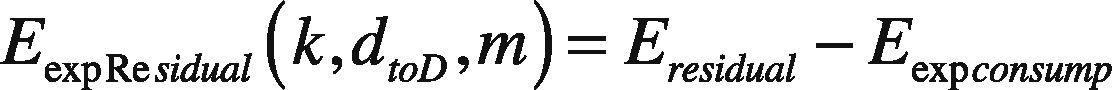Mobile Ad hoc Network consists of mobile nodes without any assisting infrastructure. Mobility of nodes causes network partition. This leads to heavy overhead and less packet forwarding ratio. In this research work, Residual Energy based Reliable Multicast Routing Protocol (RERMR) is proposed to attain more network lifetime and increased packet delivery and forwarding rate. A multicast backbone is constructed to achieve more stability based on node familiarity and trustable loop. Reliable path criterion is estimated to choose best reliable path among all available paths. Data packets will be forwarded once the reliable path is chosen. We have also demonstrated that residual energy of paths aids to provide maximum network lifetime. Based on the simulation results, the proposed work achieves better performance than previous protocols in terms of packet reliability rate, network stability rate, end to end delay, end to end transmission and communication overhead.
Mobile ad hoc network is the kind of wireless ad hoc networks where it does not need any infrastructure. The information about neighbour nodes is communicated via wireless links with no access point. Compared with wired networks, MANET does not cost for network design, construction and management. It has the potential to improve fault tolerant with the help of distributed control mechanism. But it is very hard to provide reliable communication because of frequent path failures. It leads to network partition and unreliability.
Packet forwarding is a major issue in ad hoc networks. It was implemented with geographic positioning protocols (Aamir & Zaidi, 2013), buffer management (Sreedevi, Narasimha, & Seshadri, 2012) and multipath delivery scheme (Lou, Liu, Zhang, & Fang, 2009), etc. Both network coding and opportunistic routing (Lee, Nam, & Jeon, 2014) were deployed to enhance data delivery rate and prolong the network lifetime. However, these schemes suffered from network unbalancing, frequent route failures and high overhead. To provide a consistent data transmission, a reliable data delivery method is required to support an unpredictable network topology and ad hoc nature.
In the proposed protocol, a stability model is integrated with optimized multicast backbone to monitor and improve the quality of link as well as node stability. The data delivery rate is improved with the chosen reliable paths. Residual energy estimation is calculated for choosing mobile nodes to prolong the network lifetime.
1.1. Challenges in Packet ForwardingThe following challenges obstruct the efficient packet forwarding during route maintenance phase.
- •
Frequent Link Failures. The link failures occur frequently due to the high mobility of nodes in the network environment. Hence the heavy packet losses may likely to occur.
- •
Path Instability. In ad hoc environment, nodes are moving randomly and communicate with wireless links. Sometimes low Signal to Noise Ratio (SNR) leads to the path instability.
- •
Packet Forwarding Attacks. Attackers in MANET environment affect the data forwarding during transmission phase. This makes slow packet transmission, duplicate data forwarding and forwarding packets to the unknown destination.
- •
Dynamic Topology. In MANET, the topology is dynamic. The nodes are randomly moving which leads to network partition. Because of this, packet forwarding rate will not be improved.
The paper is organized as follows. Section 2 describes the related work that focus on previous approaches for data forwarding. The drawbacks are also analyzed in this section. Section 3 explores the proposed work implementation. Section 4 provides the simulation results and last section concludes the proposed work.
2. Related WorkReliable Multicast Transport Protocol (Paul, Sabnani, Lin, & Bhattacharyya, 1999) was developed to reduce the acknowledgement traffic and end to end latency using local recovery and grouping receivers. The overall hierarchy was converted into multi-level hierarchy where the packet throughput was improved using selective repeat transmission mechanism. The probability of retransmission of lost packets has also been dealt in this work. Dynamic Ring based Multicast Routing protocol was presented (Zhou, Li, Zhan, Mao, & Hou, 2004) where the radius of the ring can be adjusted according to the route maintenance. Expanding Ring Search (ERS) mechanism was used to recover the member nodes during path breakage conditions. This protocol was proved the scalability. But in this work, the performance of the system is low during high mobility environments. In this work (Yang, Yeo, & Lee, 2012), the author proposed efficient Position based Opportunistic protocol based on stateless geographic routing property and broadcast nature. The protocol provides with virtual destination based void handling to avoid the communication holes. In case of link breakage, selecting forwarding nodes were specified. A multicast data forwarding scheme (Kim, Ahn, & Lee, 2005) was used in multi-hop wireless networks which does not support routing loops or packet duplication. The author introduced a table for the prevention of packet duplication in multicast tree based routing protocol. It achieved high packet delivery rate than mesh based routing. Robust and Secure Routing scheme (Vaidya, Yeo, Choi, & Han, 2009) intended for highly dynamic ad hoc networks to compute node disjoint paths. The author discovered the path reliability and security to achieve highly secure network routing. A new scheme for buffer management (Aamir & Zaidi, 2013) achieved packet queues through active queue management strategy. All the neighbor nodes shared the buffer space. Packet transmission with low data rate was attained. Efficient Geographic Multicast Protocol (Sreedevi et al., 2012) used the virtual zone based structure to implement scalable and efficient group membership management. The overhead was also reduced during route searching and route maintenance process based on node position information. In this routing, network progression is not implemented. SPREAD (Lou et al., 2009) reached more secure end to end delivery service based on security enhancement scheme. The optimal share allocation schemes were utilized for certain degree of reliability. A mesh based multicast routing scheme (Biradar, Manvi, & Reddy, 2010) found the stable multicast path from source node to destination node. The stable forwarding nodes are chosen based on high stability of link connectivity nodes. In (Lee et al., 2014), the author proposed both cluster based approach and location based approach, to prevent the control traffic and to define each cluster area. The relationship between mobile nodes and cluster area suitable size was determined. MAC-independent Opportunistic Routing and Encoding (MORE) (Kashihara, Hayashi, Taenaka, Okuda, & Yamaguchi, 2014) was introduced to improve reliable communication. Both location information and the transmission probability were used for efficient delivery of packets. In this method, all of the nodes can hold the latest Neighbor Nodes information within two hops by updating periodically. A new contention-based enhanced distributed channel access (EDCA) scheme and token bucket algorithm (Yanbin & Yulin, 2009) were combined which provides a probabilistic QoS support and to adjust the contention window. This scheme provides traffic differentiation. A routing scheme was proposed (Srinivasan & Kamalakkannan, 2013) based on route stability and residual energy metrics during route discovery and maintenance. It computes the link stability based on measurement of received signal strength of successive packets and route stability is to satisfy required energy metric to act as intermediate nodes. New-Location-Aided Routing-1 was proposed (Gupta & Gupta, 2014) for reducing energy consumption in MANET. It achieved energy conservation along with sending successfully higher data packets to the destination. The optimal routing algorithm was proposed (Acer, Giaccone, Hay, Neglia, & Tarapiah, 2012) to achieve high delivery rate in realistic bus network through minimizing the expected traversal time and maximizing the delivery probability over an infinite time horizon. The hybrid Content Delivery Network (CDN) system was proposed (Kim, Lee, & Choi, 2013) to combine novel content routers in underlay with the server in overlay. It employs the prefix caching and the multicast schemes respectively. Bandwidth Delay Product (BDP) based multicast routing scheme (Biradar & Manvi, 2012) was proposed for ring mesh backbone based on mobility, remaining battery power and differential signal strength. The node pairs are used to compute BDP between them. The reliability pair is assessed using available bandwidth and delay experienced by a packet between them. Backbone ring mesh is constructed using reliable pair nodes and convex hull algorithm. Reliable ring mesh is constructed at an arbitrary distance from the centroid of the MANET area. In case of node mobility and failures occurs, the ring mesh can be able to maintain high BDP on ring links and also it can be recovered. In (Sung-Ju et al., 1999), On Demand multicast Routing protocol was developed to build routes and maintain multicast group membership. But, the stability of routes was not considered to defend against malicious activities. In the proposed approach, the protocol can withstand all attacks and environmental defects. In Moustafa and Labiod (2003), the performance comparison of multicast protocols was analyzed through simulation results. Among that, Source Routing Multicast Routing (SRMP) achieved better performance based on node selection criteria during mesh construction. But the probability of choosing reliable path is low in SRMP. In our previous work (Rajaram & Gopinath, 2014), optimized multicast routing scheme has been introduced to attain more network stability. In this work, the estimation of link stability, path stability and node stability is determined to provide more network stability. The trustable network was formed based on stability model.
In Aquino-Santos et al. (2010), authors presented a performance analysis of an enhanced version of the Topological Multicast Routing Algorithm (ToMuRo). It included undecided border nodes. The undecided border nodes were used to forward multicast packets to optimize the path discovery process. It was done by choosing undecided nodes that can function as multicast relay nodes. But in this work, there was no stable and reliable model enhanced to support optimum routing packet delivery.
In Jamali, Rezaei, & Gudakahriz (2013), authors considered routes length in its route selection process and also includes routes energy level in its calculations. It formulated the routing issue as an optimization problem and then employed Binary Particle Swarm Optimization algorithm to choose a route that maximizes a weighted function of the route length and the route energy level.
The proposed protocol aim is to arrive at a multicast protocol which strikes a balance between path forwarding and residual energy.
3. Overview of Energy Based Reliable Multicast Routing ProtocolIn the proposed protocol, source nodes find all the remaining nodes through multicast routes. The paths are found with more energy and stability. Packets are forwarded through the proposed path reliability criterion. Energy consumption is minimized through the energy model.
3.1. Network ModelIn the proposed model, it is assumed that nodes are moving within transmission range. Network topology is represented by G (K,L), when K (Vertices) & L (Edges) are the set of mobile models & wireless links. Nodes forward the packets via multicast routes Viz. R. Mobile modes are assigned with unique identifier individually. The packet delivery rate is ∑(S,D) (where S and D are the sending and receiving nodes).
To improve the packet forwarding rate, the following assumptions are made:
- 1.
The message should be delivered in multi-hop behavior.
- 2.
Packets should be transmitted through reliable link.
- 3.
The link error probability should satisfy the transmission power.
- 4.
If transmission power is adjusted, the data delivery rate should not be changed.
If nodal degree is getting increased, the number of packets destination should be N(n,h) ≥ N(k,h) ≥ 0. If the nodal degree is high, the packet rate will be increased.
Packets should be forwarded based on random walk. It is described as 0 ≤ N(k,h) – N(k,g) ≤ N(l,h) – N(l.g), where g,h,k,l,n,k are the mobile nodes with same transmitted region. N indicates the number of packets.
The high deliver rate criterion can be achieved based on:
- •
Packets to the destination should be successfully delivered with reduced losses.
- •
Link connectivity should be maintained during route discovery and route maintenance phase.
- •
Source node and destination node should follow the path reliability rate and packet forwarding strategy.
- •
Choose high stable nodes and reliable paths to the destination with least hop distance.
In the proposed scheme, the route discovery process is initiated by whenever the source node doesn’t have a known route to the destination. The process is divided into three stages:
- 1.
Front end stage.
- 2.
Intermediate stage.
- 3.
Back end stage.
In front end stage, some nodes flood the control packet which contains node location status to the destination. The node which satisfies high delivery rate criterion, that can join node rate (R1,…R2…Rn). If a node doesn’t satisfies, it takes time to achieve criterion. To avoid looping, route record will be installed in all nodes ID.
In intermediate stage, all the nodes can join or leave based on high delivery rate criterion. All the nodes keep the route break field which intimates the cases of link, route failures to destination and source node.
In back end stage, the destination nodes send the packets through intermediate nodes. Route error message will be generated when Acknowledgement (ACK) packets are not received.
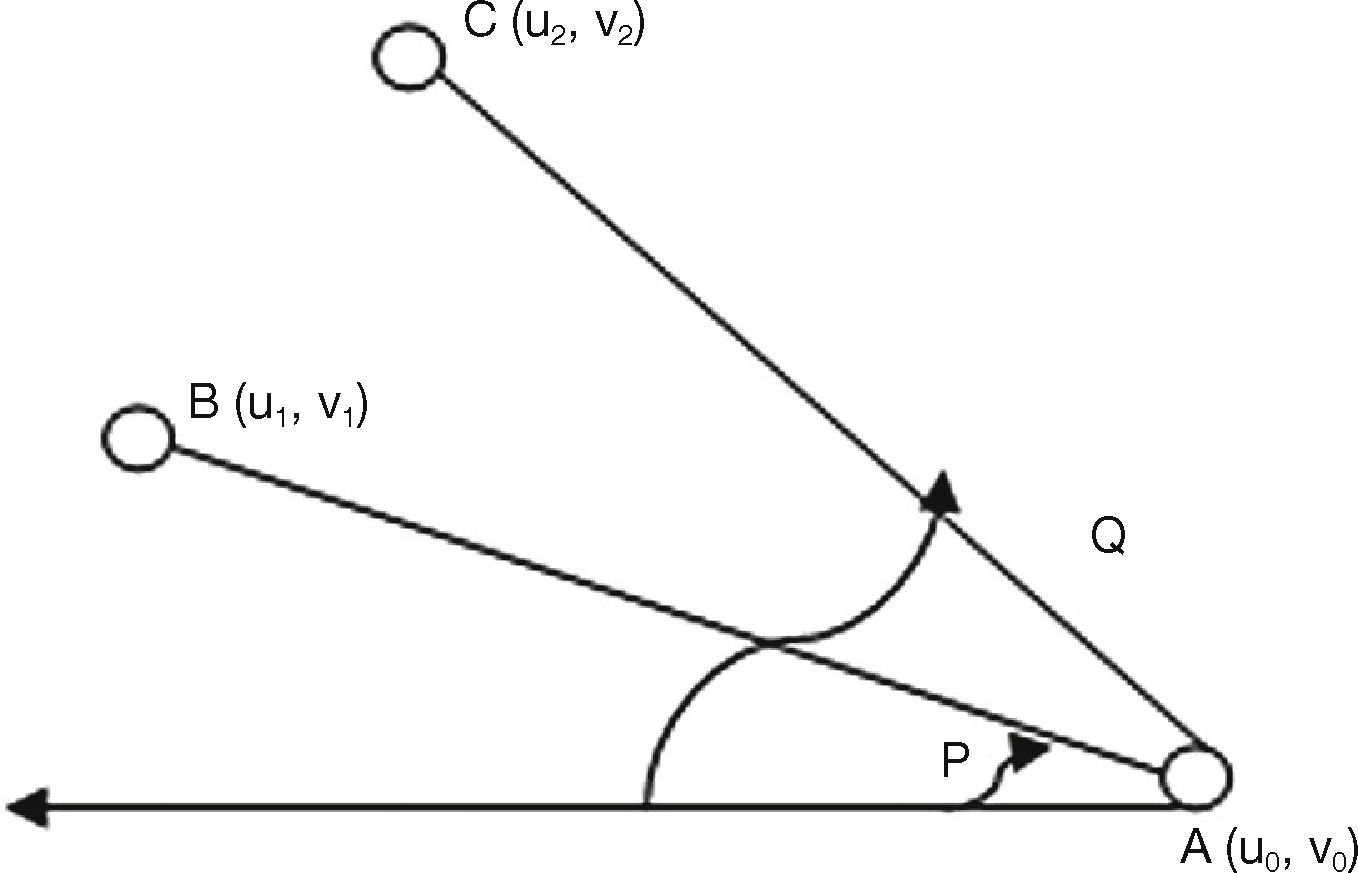
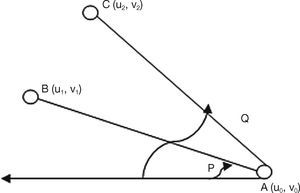
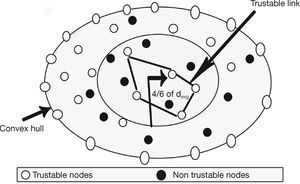
3.2. Optimized Multicast Backbone ConstructionOptimized multicast route acts as a backbone in MANET. To create this backbone, it is required to have a complete topological knowledge. The MANET boundary area is determined by using the jarvi's convex hull algorithm (Biradar & Manvi, 2012) from computational complexity. If the boundary is known, the area and centroid can be determined, which helps in the construction of backbone. In Figure 1, the convex hull creation is illustrated. The angles P, Q correspond to two extreme neighbors on negative x-axis. An angle is supposed to calculate at node A(u0, v0) that is assumed to be a starting node to initiate convex hull formation on all the boundary nodes.
The angle at A(u0, v0) selects a neighbor node B(u1, v1) as it makes minimum angle P rather than neighbor node C(u2, v2) which makes an angle Q with the condition that P
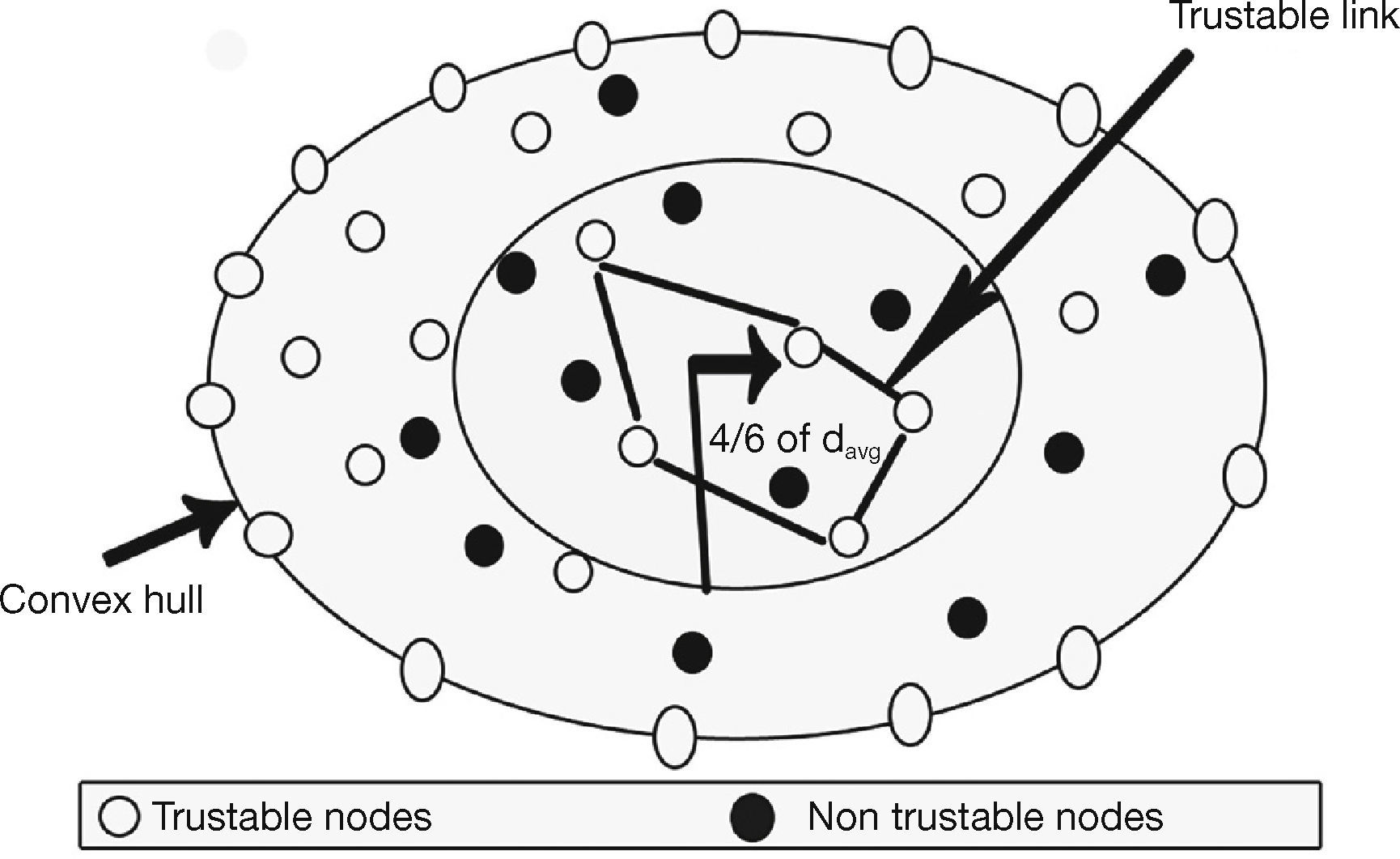
This procedure is repeated at node B and its next boundary node (tracing all the boundary nodes) till it reaches to the original node A(u0, v0) through opposite direction. Thus, the convex hull is created. Once the convex hull is created, optimized multicast back bone can be constructed to balance network reliability and residual energy. The creation of optimized multicast backbone is shown in Figure 2. Optimized multicast creation is initiated based on two assumptions:
- 1.
Establishing a trustable loop that should be located at 4/6th of an average radius from the centroid so as to be reached by all the nodes with least hop distance whether they are either towards the centroid or towards the boundary nodes on the convex hull.
- 2.
The loop is formed by connecting links formed by trustable factors of node familiarity, node proposal, link stability and path stability (Rajaram & Gopinath, 2014).
Average radius is obtained by:
where N = number of nodes and ui, ui', vi, vi' are the convex polynomials created by nodes. The optimized multicast routing is constructed at an arbitrary distance daverradius measured from centroid of the convex hull. It is given by davg=46×daverradius. All the nodes at davg are joined together to form an optimized backbone.
3.3. Multicast Group MaintenanceDuring multicast group maintenance, the multicast groups can be overlapped if they meet each other while moving according to the group mobility. Each group can be divided into several groups. In the proposed multicast architecture, the mobile nodes are performing the task allocated to the group. It does not need to consider a merge or a split between groups because one group can only be divided into several temporarily, and two groups can meet for a short time. If the leader or cluster head of the group dies, none of the mission group members can receive data from the multicast source. So, the sub-leader of the multicast group checks if the RERR message has arrived within a threshold of latency. If the sub-cluster head does not receive a RREQ message within a certain period of time, it assigns itself as the cluster head of the multicast group, advertises this fact to the members of the multicast group, and sends a change of leader request message to the multicast source.
3.4. Data Forwarding Through Reliable PathDue to mobility of nodes, topology changes frequently and unpredictably. If node moves out of transmission range, then the alternative path must be found to forward the packets immediately. If the packets would not be able to be relay to the neighbor nodes with less node degree, the route discovery process will be reinitiated by source to find a new route to the destination. When some of the neighbor nodes or destination node moves out of range, the path maintenance will be initiated to correct the broken links. Once node locality identified, the upstream node of broken path will send RREQ messages to the destination. Otherwise it will send the Route Error (RERR) message to destination and then it will choose alternative path to send ACK messages, otherwise it requests source to reinitiate route discovery. The path reliability criterion is useful to choose the best path for packet transmission. If many paths are available, the route with path reliability is desired.
The path reliability criterion (PRC) can be calculated as:
where k = number of hops that the link carries, p1,p2......P is the number of packets travelling along the path, LER is the link expiry rate, used to determine the link lifetime, and PLR is the packet loss rate.
The advantage of the path reliability criterion is to choose a higher quality path with minimum number of retransmissions, minimum energy consumption and network lifetime improvement.
To efficiently deliver the data, source node generates the forwarders list which specifies the neighbor relay node that forwards a packet via reliable path. Source node floods the data packets with forwarders list. The data packets contain geographical position of source node and destination node along with next neighbor forwarding node information. The forwarders list is always updated in hop by hop fashion and its size depends on number of forwarding neighbor nodes. The relay node can be replaced with new relay by means of changing forwarders list with the new one. In network, each path link has a packet error rate indicator to find packet duplication or not. It is desired to choose path which has links with higher quality and lower bit error rate to increase packet transfer reliability. Based on the path reliability criterion, the reliable path can be chosen among several paths to maximized data forwarding rate.
3.5. Estimation of Residual EnergyDue to frequent path breakdowns, it is necessary to choose the mobile nodes with more residual energy. Before the optimized multicast backbone construction, the number of mobile nodes is unknown. Once multicast backbone creation is finished, nodes communicate and send their data to source node at most once per frame during allocated transmission slot. The number of frames can be obtained as:
where top is the operation time of source node to send the data packets, τslot is slotted time required for the transmission from source node to neighbor node, and τNtoD is the time required for the transmission from neighbor node to destination node.The expected energy of a node to reach source node after the operation time could be represented as:
It is assumed that all the mobile nodes transmit and receive the same size of packets, i.e. k bits of data. The distance (dtoD) to the destination could be computed based on received signal strength. The expected residual energy (EexpResidual) of a mobile node during mobility conditions:
Eresidual is the residual energy of a mobile node before the route discovery process. Among several paths, the path with “High expected residual energy (HERC)” parameter will be given with higher priority for packet transmission. The factor RE is used to indicate energy consumption before and after route discovery process and it is expressed as:
The initial value for this factor is initial energy (EI). The proposed protocol can reduce the route request packets and packet loss with our stability model (Rajaram & Gopinath, 2014) in the presence of energy dissipation of mobile nodes. Consequently, more residual energy can be saved for relaying the data packets instead of being wasted on excessive path discoveries.
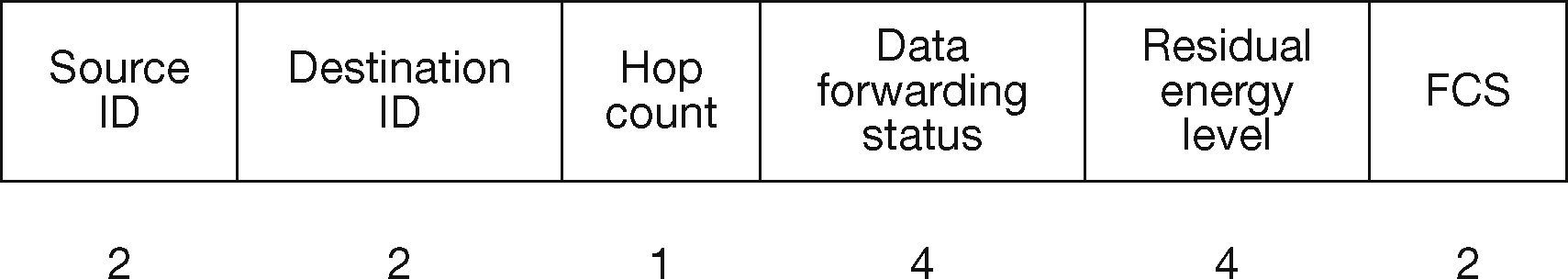
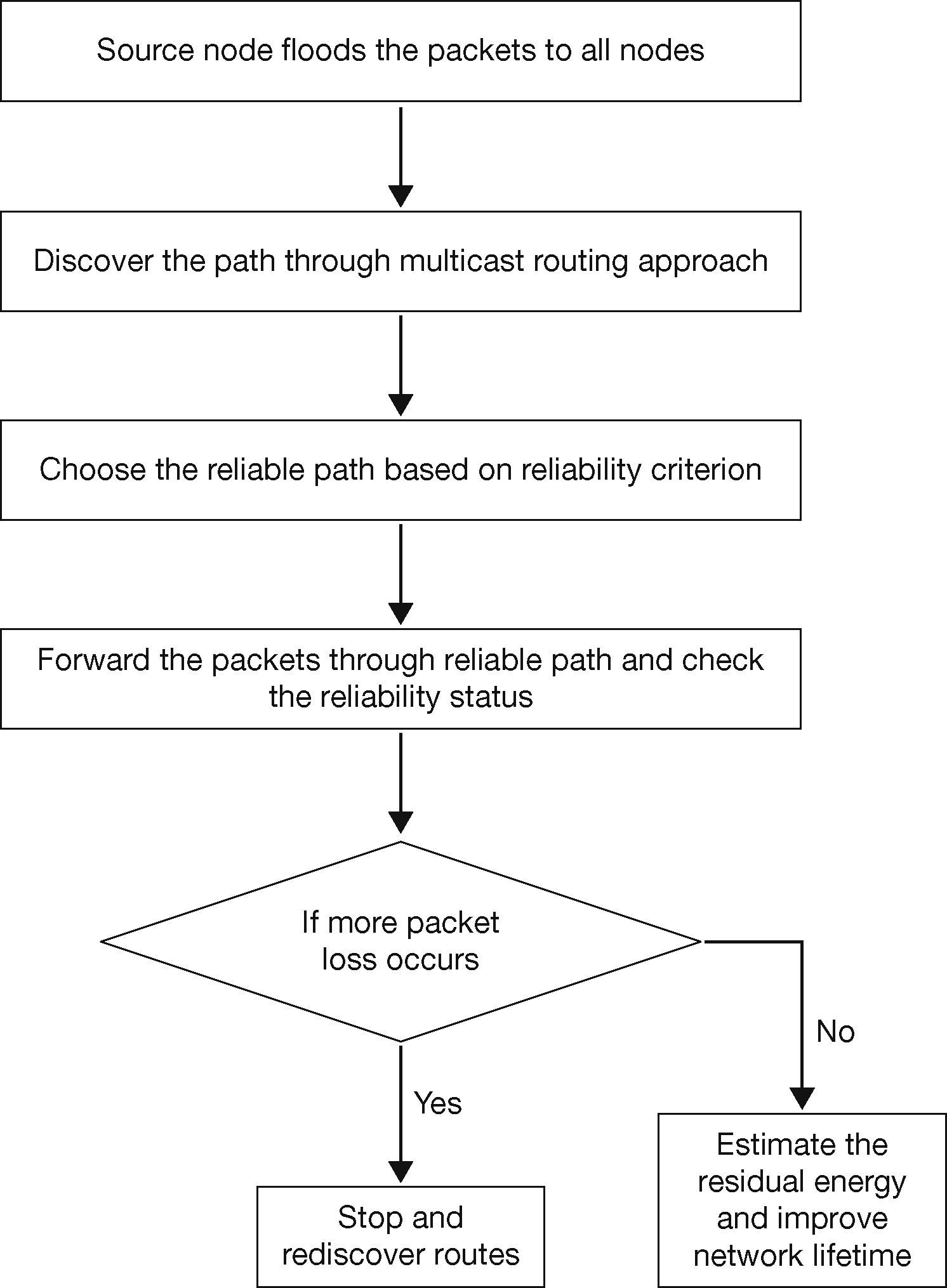
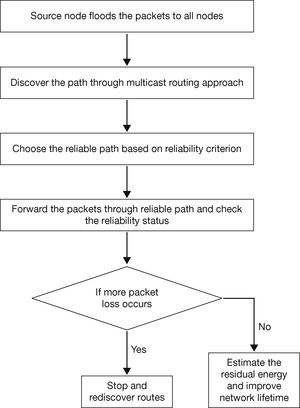
3.6. Packet Format of RERMRIn Figure 3, the proposed packet format of RERMR is shown. Here the source and destination node ID carries 2 bytes. The third field hop count determines the number of n does connected to the particular node in the cluster. It occupies 1 byte. The data forwarding status occupies 4 bytes. Each mobile node checks the fifth field, i.e. residual energy level of other remaining mobile nodes. The last filed FCS (Frame Check Sequence), which is for error correction and detection during packet transmission. The flow chart of the proposed protocol operation is shown in Figure 4.
3.7. Description of RERMROverall operation of proposed protocol is illustrated in Figure 4. The proposed scheme is to identify the optimal route in the network. For that, optimized multicast backbone is constructed to find the trustable and non trustable nodes using the link and node stability ratio estimation. The node stability, link stability and path stability (Rajaram & Gopinath, 2014) are used to identify the optimal multicast route. Estimation of residual energy and path criterion is shown to improve the network availability and prolong the network lifetime.
4. Performance EvaluationThe performance of the proposed approach is evaluated in this section. The network model is discussed in section 4.1 and the simulated results are presented and described in section 4.5.
4.1. Network ModelIn the proposed network model, it is assumed that K+1 mobile node in the network while taking the source node is K and destination node is (K+1). The packets are received in a queuing order from the rest of K nodes. The proposed model is symmetric and synthetic model. Here the mobile node may in the transmission range or out of range. The packets are transmitted in a fixed size and the route discovery time is deterministic. Packets are arrived to the destination according to the Markovian Arrival Process in discrete time (DBMAP/D/1/N). Here, N is the buffer size of the destination mobile node. So, the process is in the queuing condition. Mobility nodes are randomly chosen while considering the packet loss probability which involves transition matrix is (K+1)(N+1) × (K+1)(N+1).
4.2. Mobility ModelThe mobility model we have chosen for our proposed scheme is Random Waypoint Mobility model. The node pause time is changed between in direction or speed, i.e. node starts by staying in one location for certain period of time. If the pause time is expired, the mobile node will choose a random destination and speed which are uniformly distributed between 0 and MAXSPEED. After that the node moves towards the destination at the selected period.
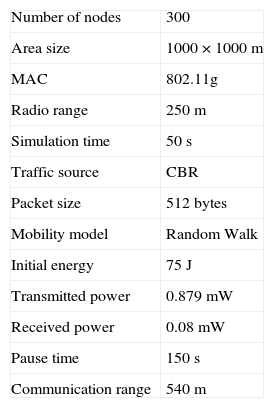
4.3. Simulation Model and ParametersWe have simulated our results using NS2.34 simulator. It is an object oriented discrete event simulator to identify the performance of proposed scheme. The Backend language of NS2.34 is C++ and front end is Tool command language (Tcl). NS2 is user friendly and easy to fabricate our own protocol. Tcl is a string-based command language. The language has only a few fundamental constructs and relatively little syntax, which makes it easy to learn. The syntax is meant to be simple. Tcl is designed to be glue that assembles software building blocks into applications. Here we made the assumption that adopted for simulation is all nodes are moving dynamically including the direction and speed of nodes. Mobility scenario is generated by using random way point model with 300 nodes in an area of 1000 × 1000 m. Our simulation settings and parameters are summarized in Table 1.
Simulation Settings and Parameters of RERMR.
| Number of nodes | 300 |
| Area size | 1000 × 1000 m |
| MAC | 802.11g |
| Radio range | 250 m |
| Simulation time | 50 s |
| Traffic source | CBR |
| Packet size | 512 bytes |
| Mobility model | Random Walk |
| Initial energy | 75 J |
| Transmitted power | 0.879 mW |
| Received power | 0.08 mW |
| Pause time | 150 s |
| Communication range | 540 m |
We evaluate mainly the performance according to the following metrics:
Average Packet Delivery Ratio. It is the ratio of the number of packets received successfully to the total number of packets transmitted.
Communication Overhead. The communication overhead is defined as the total number of routing control packets normalized by the total number of received data packets. It suppresses the communication between the source and destination nodes.
End-to-end delay. It depends on the routing discovery latency, additional delays at each hop and number of hops.
Network Stability Rate. The optimal rate of links and nodes which defends against malicious activities and environmental defects.
Packet Reliability Rate. It is defined as the ratio of number of packets which are not altered or delayed or duplicated to the total number of packets.
4.5. ResultsWe compared our proposed scheme with OMRS (Rajaram & Gopinath, 2014), SRMP (Moustafa & Labiod, 2003) and Bandwidth Delay Product based Multicast routing Scheme (Biradar & Manvi, 2012) and On Demand Multicast Routing Protocol (Sung-Ju et al., 1999).
The results are examined by using performance metrics end-to-end delay, packet delivery ratio, packet reliability rate, network lifetime, end to end delay and overhead.
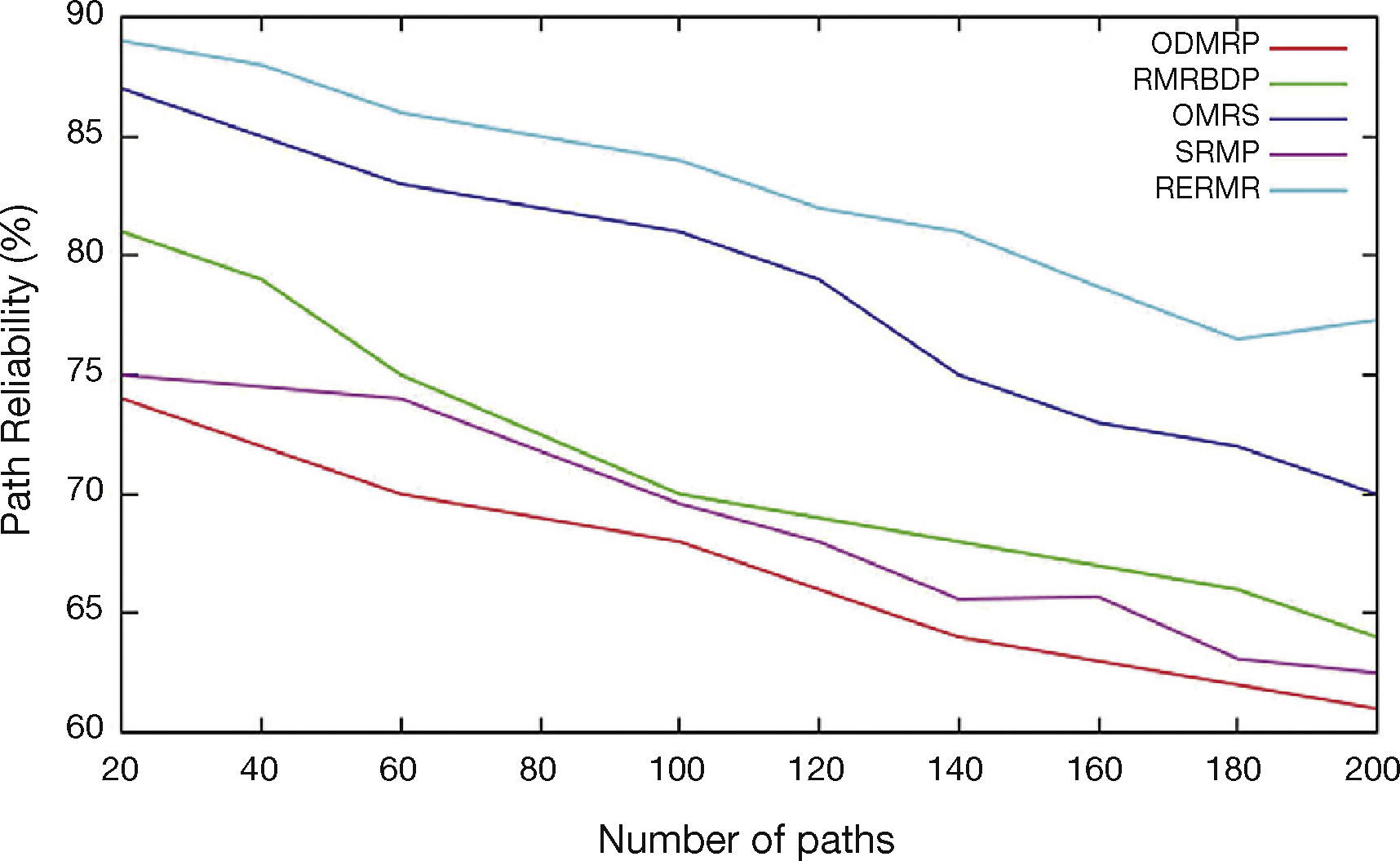
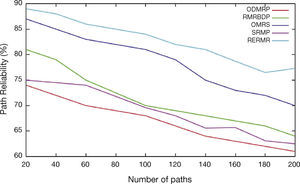
Figure 5 shows the analysis of number of paths vs. Packet reliability rate. From the results, our proposed protocol achieves high packet reliability rate than the existing schemes namely SRMP, OMRS, ODMRP and RMRBDP because of stability deployed in the optimized routing.
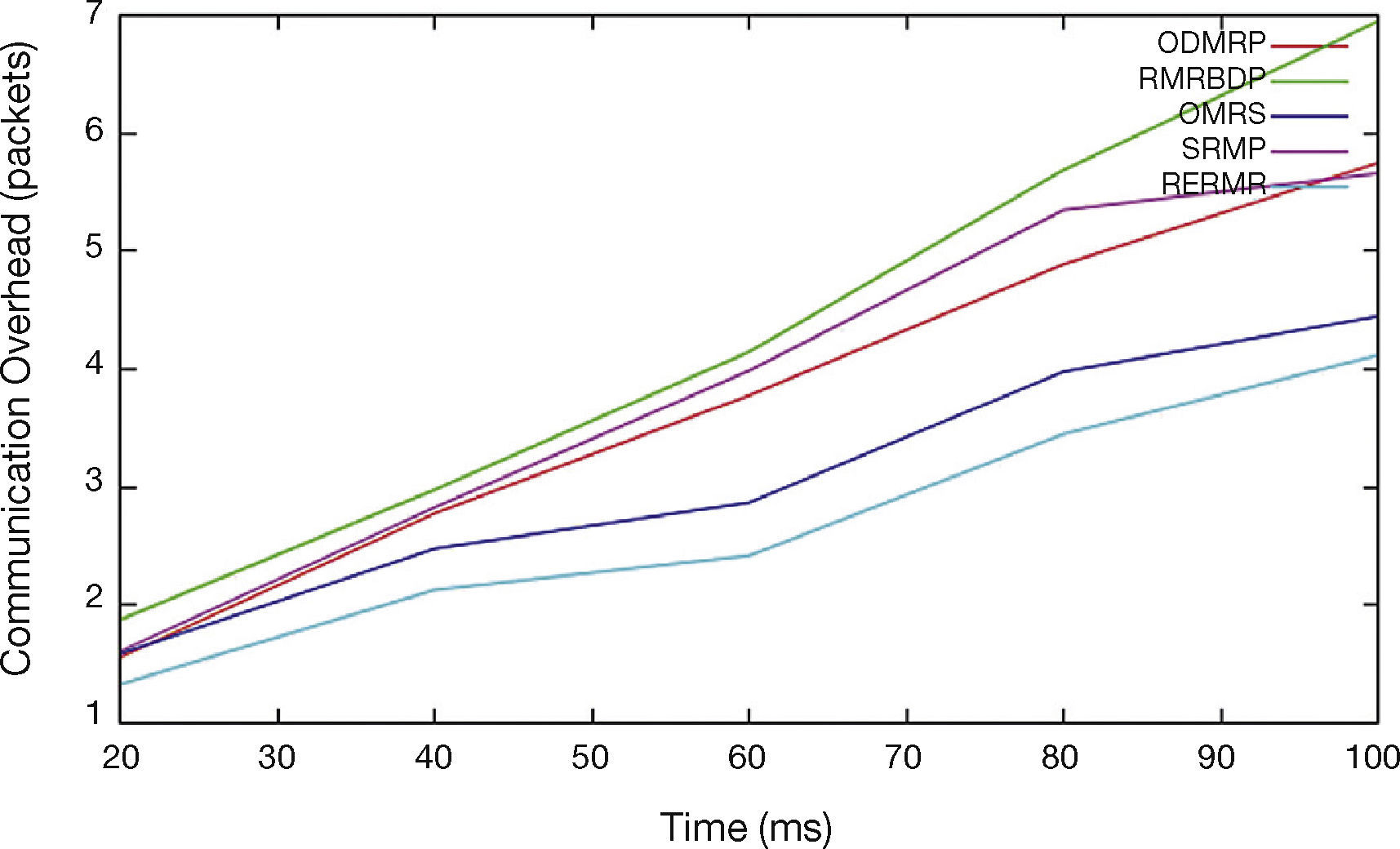
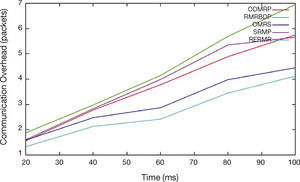
In Figure 6, we vary the time from 10 to 100. While increasing the time, the communication overhead of proposed RERMR has low than OMRS, SRMP ODMRP and RMRBDP. This is achieved by employing the trustable packet loss ratio in the transmission process.
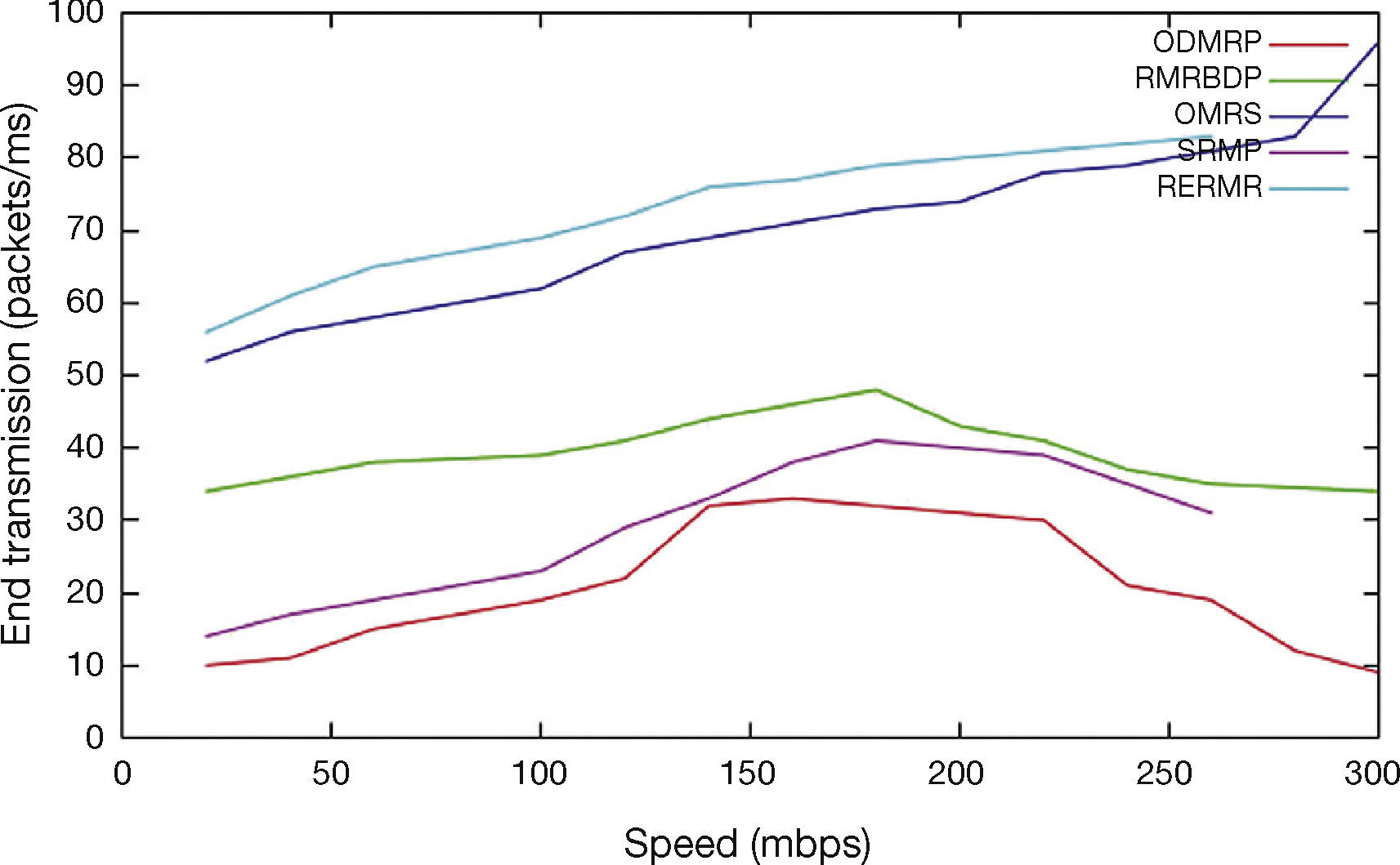
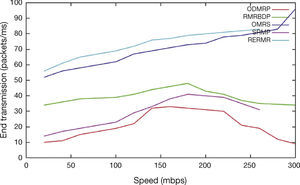
In Figure 7, speed is varied from 0 to 300 mbps. The end to end transmission of proposed scheme achieves high than OMRS, SRMP, ODMRP and RMRBDP because of high path reliability criterion.
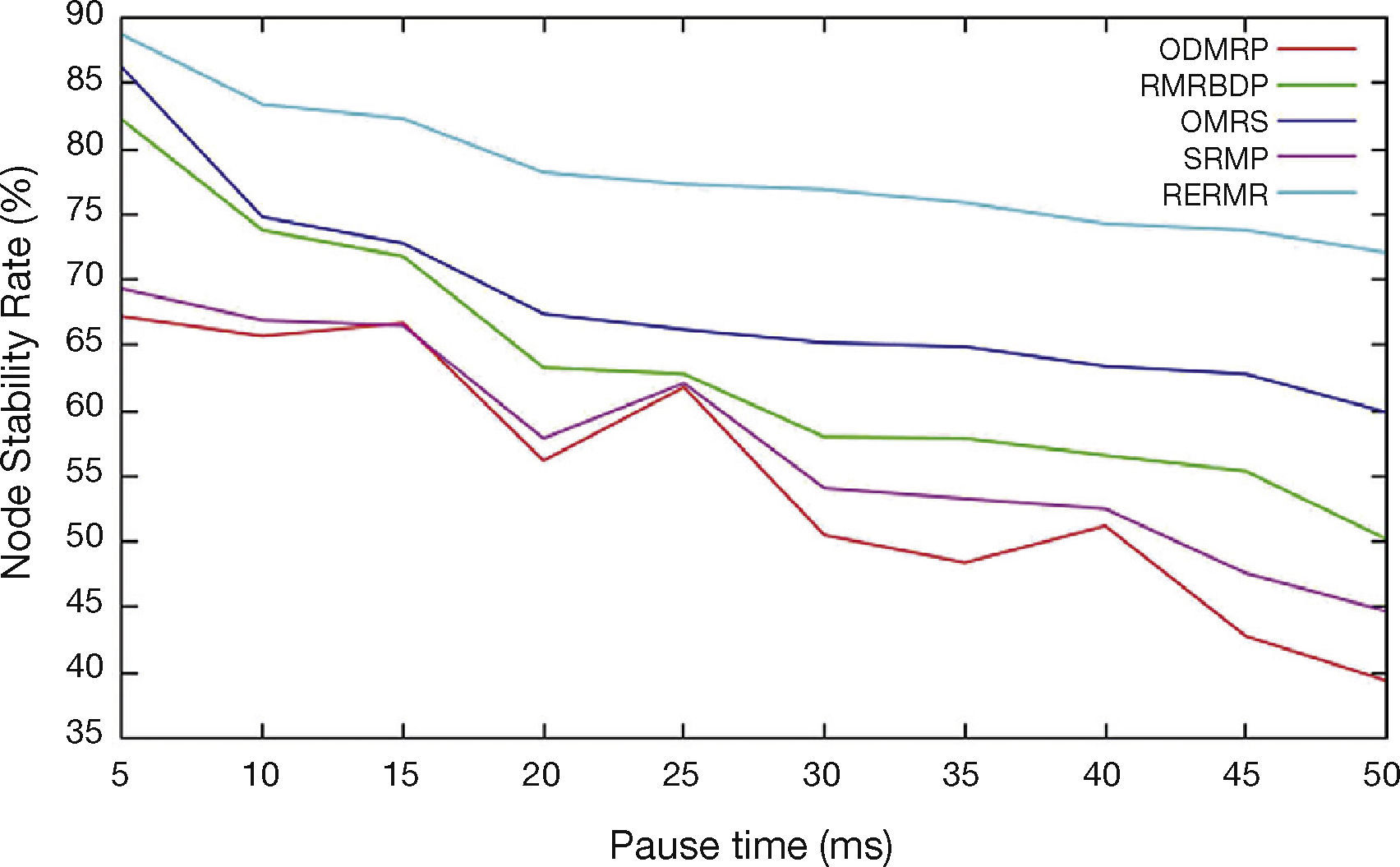
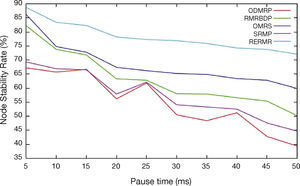
In Figure 8, we vary pause time from 5, 10,…50ms. The network stability rate of RERMR achieves higher than OMRS, SRMP, RMRBDP and ODMRP. It is because of installation of all the stable links as well as nodes.
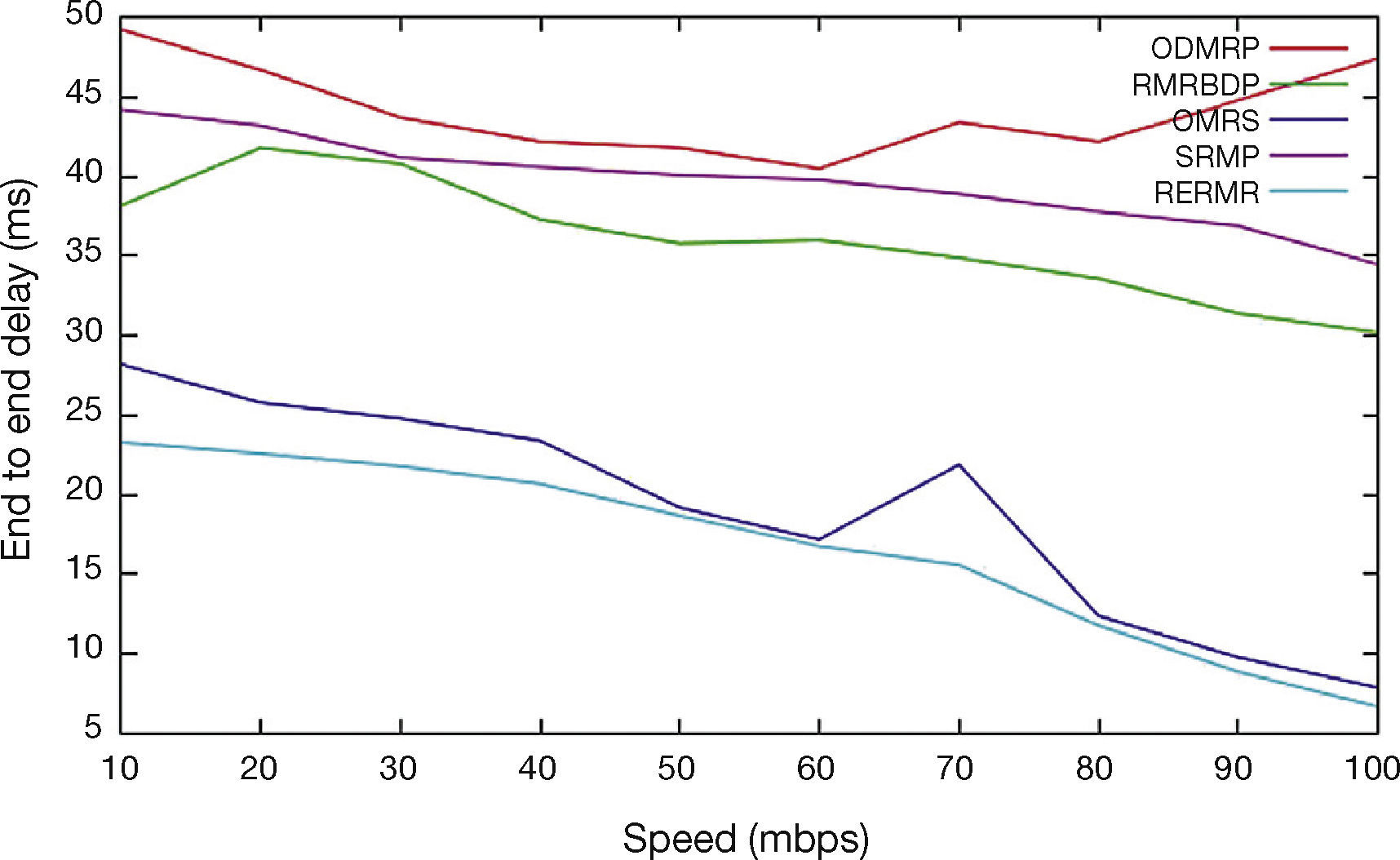
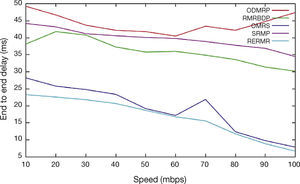
In Figure 9, speed is varied as 10, 20…100. When we increase the speed, the mobility is also getting increasing. The proposed algorithm RERMR has low end to end delay per packet than OMRS, SRMP, ODMRP and RMRBDP. The pause time is reduced to minimize the delay between the packets.
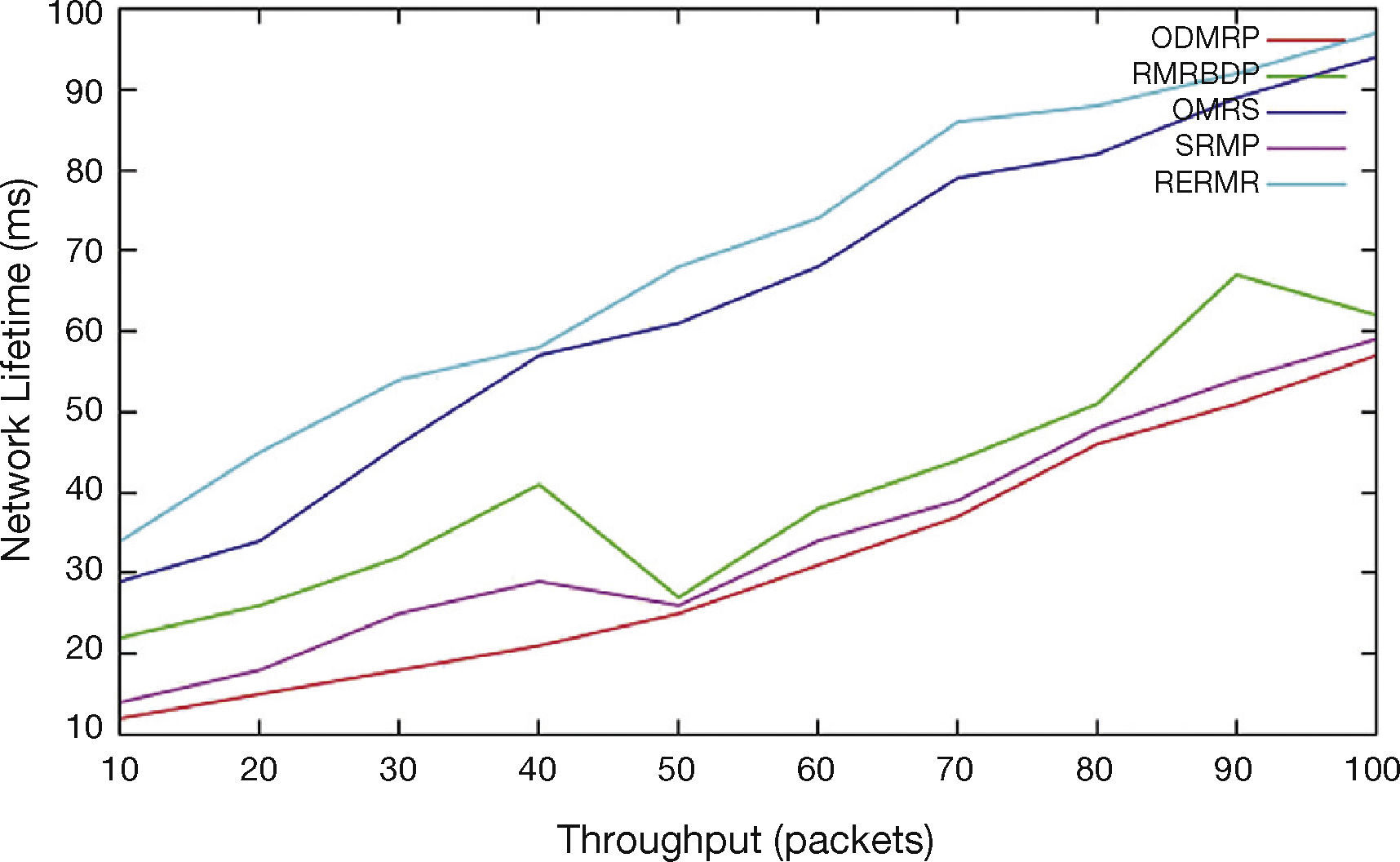
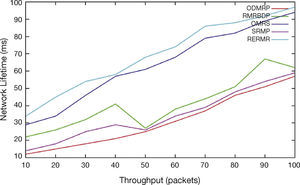
In Figure 10, throughput is varied as 10, 20…100. The network lifetime of the proposed algorithm RERMR has high Network lifetime than OMRS, SRMP, ODMRP and RMRBDP. While residual energy of the path increases, the node lifetime is getting increased.
5. Conclusions and Future workIn this research work, RERMR protocol is proposed for increasing packet forwarding, path reliability and more residual energy. The proposed protocol is based on threshold value to maintain the reliable multicast routing which enhances the stability and connectivity of the network. Network model is designed to achieve more packet delivery rate criterion. Optimal multicast backbone is constructed to improve reliability of multicast routes. Data packets are successfully forwarded through the reliable path chosen by reliability criterion. The best path is chosen based on high residual energy. By simulation results, the RERMR is better than OMRS, RMRBDB, SRMP, and ODMRP in the presence of high mobility environment. The proposed work can be a suggestive approach for a real life approach such as military search and rescue operations.
Future studies can be extended to implement the authentication and security in the optimized multicast routing scheme to provide better integrity. We plan to propose the symmetric cryptographic scheme to make network more secure.