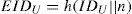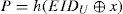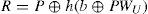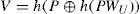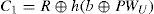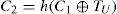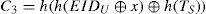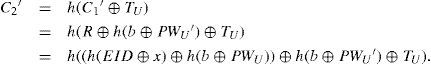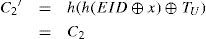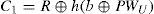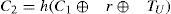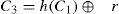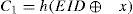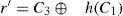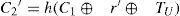Due to the open environment, all network systems suffer from various security threats. The remote user authentication scheme is a secure mechanism to allow users obtaining a variety of information services through insecure channels. For efficiency and security, many remote user authentication schemes identify users with smart cards. However, many smart card based schemes are vulnerable to lots of attacks. Recently, Hsiang et al. proposed a smart card based remote authentication scheme. In this article, we show that their scheme is vulnerable to the smart-card-loss-attack. That is, if an unauthorized person obtains the smart card, he/she can guess the correct password to masquerade as a legitimate user to login the system. The attack is caused by the smart card outputs fixed message for the same inputs. We propose an improved scheme to fix the flaw. The improved scheme withstands the off-line password guessing attack, parallel session attack and smart-card-loss-attack. Moreover, it also has the merits of providing mutual authentication, no verification table and users can freely update their passwords.
Nowadays, people obtain a variety of information or services through networks. However, due to the open nature, all network systems always suffer various security threats. The remote user authentication scheme is a secure mechanism to allow users obtaining services through insecure channels [1-4], and it is the most common method used to check the validity of the login message and to authenticate the servers or users. A lot of authentication schemes also provide mutual authentication, key agreement and freely updating password.
A remote user authentication scheme includes two main entities: servers and remote users. The communications between the servers and users are through insecure open channels. Thus, the security vulnerabilities of the remote user authentication scheme may occur due to the remote users, servers and insecure channels [5]. Many remote user authentication schemes identify users by using smart cards. However, many smart card based schemes are vulnerable to various attacks. Moreover, lots of schemes suffer the smart-card-loss-attack. The smart-card-loss-attack means an adversary can launch various attacks such as off-line guessing attack when he/she obtains a legitimate user’s smart card.
In 1981, Lamport [6] proposed the first well-known remote password authentication scheme by using smart cards. However, Lamport’s scheme has the drawbacks such as high hash overhead and requiring a password table at the server end. Until now, there are many smart card based password authentication schemes have been proposed [1, 5, 7-9] to improve security, efficiency or to reduce costs. However, most schemes still cannot solve all possible problems and withstand all kinds of attacks [10-12].
Hwang et al. [7] proposed a smart card based remote password user authentication scheme to overcome the weakness in security. However, their scheme does not allow users to freely update passwords and it cannot withstand the masquerade attack either. In 2002, Chien et al. [13] developed a remote user password authentication scheme to provide mutual authentication and freely updating password. But Ku et al. [14] showed that Chien et al.’s scheme is vulnerable to the reflection attack and the insider attack. Ku et al. also proposed an improved scheme to fix the flaws. However, Yoon et al. [15] indicated that the improved scheme was also susceptible to the parallel session attack, and then presented an improved scheme to enhance the security.
In 2009, Hsiang et al. [16] showed that Yoon et al.’s scheme is vulnerable to the parallel session attack, masquerading attack and password guessing attack. They also proposed an improved scheme to remedy the drawbacks. In this paper, we will show that Hsiang et al.’s scheme is vulnerable to the smart-card-loss-attack. If the smart card is lost, an unauthorized person can correctly guess the password and masquerade as the legitimate user to login the system. We also propose an improved scheme to fix the flaw. The improved scheme has the merits of mutual authentication, no verification table, and users can freely update their passwords. Moreover, the improved scheme withstands the off-line password guessing attack, parallel session attack and smart-card-loss-attack.
The remainder of this article is organized as follows. The notations used throughout this paper are listed in the next Section. In Section 3, we briefly describe Hsiang et al.’s remote user authentication scheme. Next, we show the smart-card-loss-attack on their scheme in Section 4. The improvement scheme and its security analysis are presented in Sections 5. Finally, we make brief conclusions in Section 6.
2Preliminaries and notationsGenerally, a smart card based remote user authentication scheme comprises the following four phases: registration phase, login phase, authentication phase and password changing phase. In the registration phase, the user sends a registration request along with related information to the server via a secure channel. The server identifies the user and generates related messages to store in the smart card, and then delivers the card to the user. In the login phase, the user attaches his/her smart card into a card reader and keys in password to login the system. In the authentication phase, the server checks the validity of the login request. If the user is authenticated, the server allows the user to access the system. In the password changing phase, the remote users freely update their passwords. Some schemes allow the server and users to obtain mutual authentication and establish a common session key.
All the notations used throughout this paper are listed as follows:
- (1)
U: A remote user.
- (2)
IDU : The identity of the remote userU.
- (3)
PWU : The password corresponding to the userU.
- (4)
S : The server of the system.
- (5)
x: The secret key of the serverS.
- (6)
h( ) : A cryptographic secure one-way-hash function.
- (7)
⊕ : The bitwise exclusive-OR (XOR) operation.
- (8)
b,r : Random numbers.
- (9)
‖: The concatenation operation.
- (10)
A ⇒B : {M} : The entityA sends a messageM to B through a secure channel.
- (11)
A →B : {M} : The entityA sends a messageM toB through an open insecure channel.
- (12)
TA :A timestamp of the entityA.
In 2009, Hsiang et al. [16] pointed that Yoon et al.’s scheme [15] is vulnerable to the parallel session attack, masquerading attack, and password guessing attack. They proposed an improved scheme to fix the drawbacks. Hsiang et al.’s scheme comprises registration phase, login phase, authentication phase and password updating phase as follows.
3.1Registration phaseIn the registration phase, the user U registers with the server S by the following steps.
Step R-1. Firstly, U chooses an identity IDU and password PWU. Then he/she computes h(PWU) and h(b⊕PWU) after generating a random number b. Next, U sends {IDU,h(PWU), h(b⊕PWU)} to S via a secure channel.
Step R-2. Upon receiving IDU,h(PWU), and h(b⊕PWU), S creates an entry for U in the account database and stores n=0 in the entry for the first registration. Otherwise, S sets n=n+1 in the existing entry for U. Next, S computesEIDU, R, R and V as follows.
At last, S stores V, R, and hash function h( ) into the smart card and sends it to U.
Step R-3. Upon receiving the smart card, U keys in the random number b into the card.
3.2Login phaseIf the user U wants to log into the system, the steps of the login phase are as follows.
Step L-1. The user U inserts his/her smart card into a card reader and keys in IDU and PWU.
Step L-2. The smart card computes C1 and C2 as follows, where TU is the user’s current timestamp.
Step L-3. U → S: {IDU,TU,C2}. The user sends { IDU,TU, C2} to the server. Note that C2=h(h(EIDU⊕x)⊕TU).
3.3Authentication phaseUpon receiving {IDU,TU,C2}, the server S verifies the login message to authenticate the user by the following steps.
Step A-1. The server S checks IDU and TU. If IDU is correct and TU is in a valid time interval, S computes C2‘=h(h(EIDU⊕x)⊕TU); otherwise, S will reject the user’s login request. If the computedresultC2‘equalstothereceived message C2, S accepts the login request and then computes C3 as follows.
Where Ts is the server’s current timestamp.
Step A-2. S → U: {TS,C3}. The server sends {Ts, C3} to the user.
Step A-3. Upon receiving the message {Ts, C3}, U checks the timestamp Ts. If Ts is in a valid time interval, U computes C3’=h(C1⊕h(Ts)) and compares C3’ with the received C3. The user U will authenticate the server S only if C3’=C3 holds.
3.4Password changing phaseIf the user U wants to change his/her password, the steps of password changing phase are as follows.
Step C-1. U inserts his smart card into the card reader and keys in his/her IDU and PWU.
Step C-2. The smart card computesP‘=R⊕h(b⊕PWU) and V‘=h(P’⊕h(PWU)).
Step C-3. The smart card compares V’ with the stored V. If they are not equal, the smart card rejects the request. Otherwise, U chooses a new password PWU_new and proceeds to the next step.
Step C-4. With the password PWU_new, the smart card computes R‘=P’⊕h(b⊕PWU_new) and V‘=h(P’⊕h(PWU_new)). Next, the smart card replaces R and V, with R’ and V‘, respectively.
4Smart-card-loss-attack on Hsiang et al.’s remote user authentication schemeThough Hsiang et al. declared that their scheme withstands the guessing attack, but recently He et al., by using differential power analysis (DPA), has shown that Hsiang et al.’s scheme is vulnerable to the guessing attack and the masquerading attack [17]. The DPA attack is a method based on an analysis of the correlation between the electricity usage of a chip in a smart card and the encryption key it contains [18].
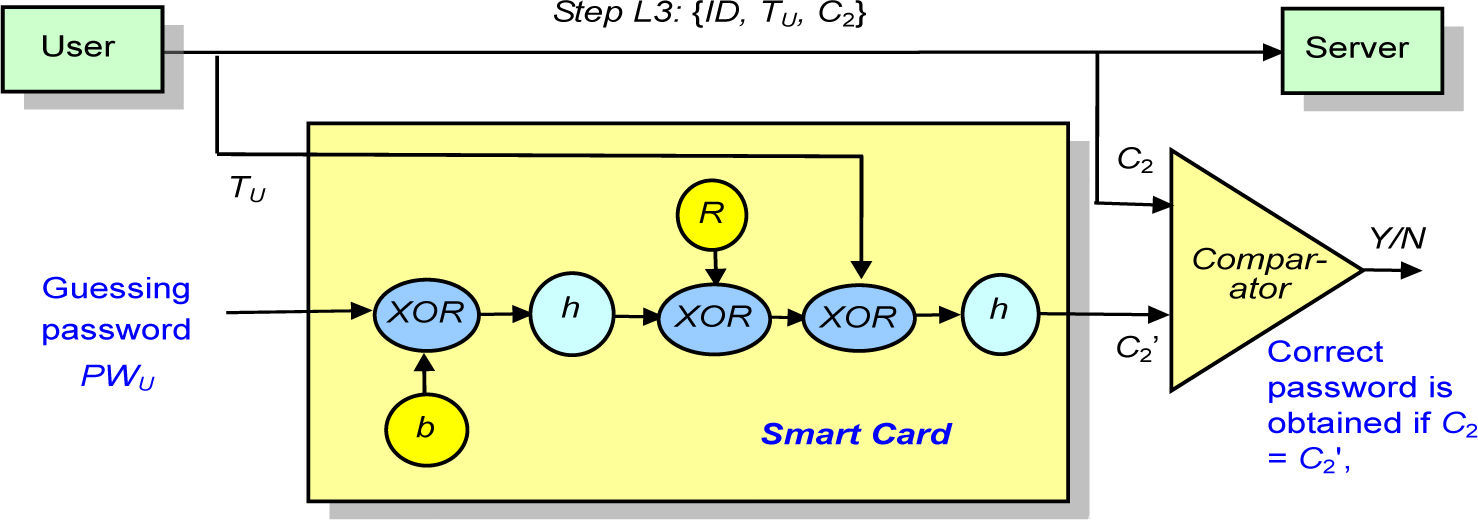
In this section, we will show the smart-card-loss-attack on Hsiang et al.’s scheme. The smart-card-loss-attack is more practical and more easily to be realized than DPA attack. We start to describe the attack by the following theorem.
Theorem 1. For Hsiang et al.’s remote user authentication scheme, the smart card will output fixed C2 if the same timestamp TU and correct password PWU are keyed into the card.
Proof. Suppose that an adversary E wants to launch the smart-card-loss-attack on a user’s smart card. E monitors the communications between the server and user. Suppose that the adversary interceptsmessageC2onalogin session, where C2=h(C1⊕TU)=(h(EID⊕x)⊕TU). Next, the adversary obtains the smart card and starts a new session of login. E keys in the guessing passwordPWU‘, and the smart card computes C1’=R⊕h(b⊕PWU’), where R and b are the secret information stored in the card and R=h(EID⊕x)⊕h(b⊕PWU). Note that PWU is the correct password used in the last login session. Hence the smart card will output C2‘, where
If PWU‘=PWU, then
That is, the smart card will output a fixed C2 if the adversary keys in the correct password and the same timestamp. The adversary can verify his/her guess of password by checking whether C2‘=C2 holds. Q.E.D.
The attack is based on the assumption that the adversary obtains the legitimate user’s smart card. The assumption is reasonable in the real world, especially for some VIPs, any adversary always wants to get the cards to obtain benefits or to hurt someone though it is illegal.
If the adversary E wants to adopt the smart-card-loss-attack on Hsiang et al.’s scheme, the steps of the attack are described in details as follows.
Step D-1. Firstly, E intercepts {ID,TU,C2} on a login session.
Step D-2. E steals the smart card or gets the card by any means.
Step D-3. E inserts the card into a card reader and keysinTU.Next, sheinputstheguessed password PWU‘.
Step D-4. The smart card computes and outputs C2‘.
Step D-5. E checks whether C2‘=C2 holds. The guessed password is correct if C2‘=C2; otherwise, E repeats the Step D-3 to D-5 until the exact password is found.
Usually, for ease of memory, the bit-length of the password is quite short. Thus it is very quickly to correctly guess the password. For illustration, the smart-card-loss-attack is shown in Figure 1.
5The improved schemeThe smart-card-loss-attack on Hsiang et al.’s scheme is caused by the smart card outputs fixed C2 when the user inputs the same timestamp and password. If the output C2 is varied on each login session for the same inputs, the attack will be avoided. The improved scheme is described as follows. Note that the registration phase and the password changing phase of the improved scheme are the same as Hsiang et al.’s scheme.
5.1Login phaseThe steps of the login phase are modified as follows.
Step L-1*. The user U inserts his/her smart card into a card reader and keys in IDU and PWU.
Step L-2*. The smart card computes C1, C2 and C3 as follows, where TU is the user’s current timestamp and r is a random number.
Step L-3*. U → S: {IDU,TU,C2,C3}. The user sends the login information {IDU,TU,C2,C3} to the server.
5.2Authentication phaseThe steps of the authentication phase are as follows.
Step A-1*. After receiving {IDU,TU,C2,C3}, the server checks IDU and TU. If IDU is incorrect or TU is not in a valid time interval, the server terminates the login steps. Otherwise, the server computes C1, r’ and C2’ by
Then the server compares C2’ with the received C2. If C2‘=C2, the server accepts the user’s login request and computes C4 by
Where Ts is the server’s current timestamp.
Step A-2*. S → U : {Ts, C4}. The server forwards {Ts, C4} to the user.
Step A-3*. Upon receiving the message {Ts, C4}, U checks the timestamp Ts. If Ts is in a valid time interval, U computes C4‘=h(C1⊕r⊕h(Ts)) and thereby compares C4’ with the received C4. The user and the server obtain mutual authentication if C4’ =C4.
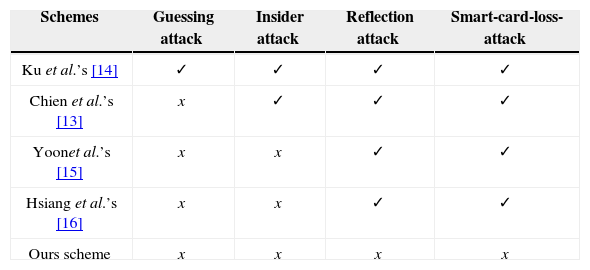
5.3Discussions and security analysisThe improved scheme has the merits of providing mutual authentication, no verification table, and freely updating password. Due to only exclusive-OR and hash function operations are adopted in the smart card, the computation cost of the proposed scheme is quite low. The pseudo random number generator is built in the computer of the user end. Thus the proposed scheme is easy and practical for implementation. A simple comparison on security among our scheme and other smart card based authentication schemes are listed in Table 1. Note that we assume that the DPA method is not adopted on all attacks, the secret information {V,R,b} in the smart card is unknown by any adversary or any malicious insiders.
The scheme withstands the smart-card-loss-attack, off-line password guessing attack, and parallel session attack. The security analysis is described as follows.
(1)It can resist the smart-card-loss-attack.In the Step L-3* of the login phase, the user sends {IDU,TU,C2,C3}totheserver, whereC2=h(C1⊕r⊕TU),C3=h(C1)⊕randC1=R⊕h(b⊕PWU). The server authenticates the user by verifyingC2. Because the random number r is included in C2, thereby C2 value varied on each login session. The ever changed C2 to result in the adversary cannot verify her guessing. Thus the improved scheme resists the smart-card-loss-attack.
(2)It can withstand the off-line password guessing attack.Suppose the adversary E wants to adopt off-line guessing attack on the improved scheme. E intercepts {IDU,TU,C2,C3} from Step L-3*. Since C2=h(C1⊕r⊕TU)andC3=h(C1)⊕r, itis infeasible for the adversary E to obtain C1 or r from C2 and C3. Similarly, if E intercepts {TS, C4} from Step A-2*, it is also difficult to recover C1 or r due to C4=h(C1⊕r⊕h(Ts)). Even if C1 or r are knownbytheadversary, duetoC1=R⊕h(b⊕PWU), it is also difficult for the adversary to guess password since R and b are unknown. Thus the improved scheme withstands the off-line password guessing attack.
(3)It can avoid the parallel session attack.Parallel session attack is resulted from symmetric computations of response messages on both the server and smart card ends. In the improved scheme, suppose that the adversary E wants to mount the parallel session attack by initiating a parallel session. When a legitimate user U sends the login request {IDU,TU,C2,C3}totheserver,Ealsosends {IDU,TU‘,C2,C3} to the server. However, the server will check C2 to authenticate the user. Note that C2=h(C1⊕r⊕TU), thus the parallel session attack will be detected by the server with the following two cases: (1) If Tυ’=Tυ the replay request is detected by S due to the presence of the same timestamp; (2) If TU’ ≠Tυ the parallel session attack will be detected by checking C2. Thus the improved scheme withstands the parallel session attack.
6ConclusionsSmart card based password authentication scheme is a very widely used mechanism to allow users to access information or services through networks. However, many smart card based password authentication schemes are vulnerable to the smart-card-loss-attack. That is, an adversary can launch various attacks to get benefits or to hurt the cardholder when he/she obtains the smart card. The main contributions of this paper are:
- (1)
We have shown that Hsianget al.’s remote user authentication scheme is vulnerable to smart-card-loss-attack. If an unauthorized person obtains the smart card, he can guess the password to masquerade as the legitimate user to login the system.
- (2)
We have proposed an improved scheme to fix the flaws. The improved scheme has the merits of providing mutual authentication, no verification table and users can freely update their passwords. The improved scheme can resist the smart-card-loss-attack, off-line password guessing attack and parallel session attack.
This work was partially supported by the National Science Council of the Republic of China under the contract number NSC 101-2632-E-274-001-MY3.